Michael Lee
Satoshi Kawamura
Otto Borchert
Wireless Security Links
Initial Proposal
First Progress Report
An access point is the gateway to the wired network, where the data transmitted by using radio waves reaches to access to another network. Because radio waves travels through the building, transmitted data may reach unintended recipients, which may cause several security problems related to the wireless access point. Some of these problems are common with the wired network, but some ot them are unique to the wireless network.
Probably the first approach to hack the wireless network is to locate the access point which is vulnerable to attack. Surprisingly, the cheap pringles can will you help to detect such access points because of its aluminum inner lining, which acts like a satellite dish. The description of the pringles can antenna is found on O'Reilly Network's web site. Properly made, such an antenna can boost the signal strength to aid in spotting wireless networks. According to BBC News, many wireless networks found with the aid of antenna made of pringles can detected access points where the encryption system was turned off. It is easily expected that such an access point can be a target of hackers. The easiest solution for this problem is simply to turn on the encryption system for your wireless network.
In my opinion, wireless networking is similar to a wired network transmitting the data through a shared bus. Such a network implements packet dropping mechanisms within hardware. I believe it can be applied to wireless networks to prevent spam from untrusted clients.
According to Extreme Tech, radio signal interference degrades network performance. 802.11b is operated in the 2.4GHz range, which is shared with 2.4GHz cordless phones, microwave ovens, and Bluetooth networking devices. The possible result of interference is packet loss from collisions, and consequently retransmitting data. This signal interference can be a potential threat to the availability in terms of security because malicious user can intentionally use the conflicting channel to reduce the performance. Besides the hacker, there are technical issues in security with 802.11b. Access points based on 802.11b have a total bandwidth of 80-MHz, which is divided into eleven center channels. Each center channel covers 22 MHZ within 80-MHz bandwidth. In other words, threre are only three non-overlapping channels out of the eleven channels. These 3 channels will be enough to cover a two dimensional area, but they are not enough to cover a three dimensional area. Jim Louderback explains this problem in his article, and suggests the alternative solution by using 4 channels to cover 3 dimentional area. I believe his solution is a solution to the availability attack because the structure he suggests will make it easier to locate the conflicting access point.
Some WLAN support authentication based on the physical address, or MAC address of the Network Interface Card. An access point will allow a client access to the network if the client's MAC address matches an address in an authentication table used by the access point. But MAC authentication is not an adequate security implementation because MAC addresses can be forged, or a NIC can be lost or stolen.
Wireless networks that use one-way authentication mechanism are vulnerlable to man-in-the middle attacks. By using rogue devices, such as access points, hackers can intercept transmissions and gather confidential information, copy or modify packets, and retransmit as valid packets. To prevent man-in-the middle attacks, mutual authentication is necessary. For this reason, Cisco created an authentication scheme based on the Extensible Authentication Protocol (EAP) called EAP-Cisco Wireless or Cisco LEAP. Cisco LEAP supports mutual authentication between the clinet and the backend Remote Autehntication Dial-In User Service (RADIUS) server. With this method, the credentials used for authentication, such as a log-on password, are never transmitted without encryption, over the wireless medium.
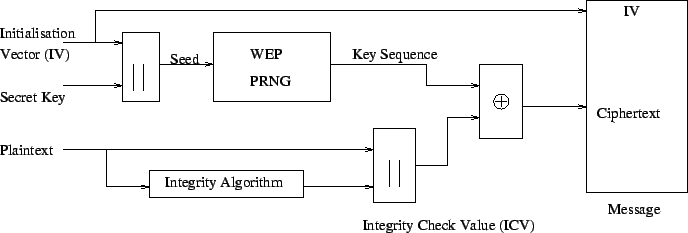
802.11 defines an optional WEP mechanism to provide confidentiality and integrity of traffic in the WLAN. WEP is used at the two lowest layers of the Open Systems Interconnect (OSI) reference model, data link and physical layers; thereby, it does not offer end-to-end security. WEP depends on a secret key shared between the communicating parties (mobile station and AP) to protect the payload of a transmitted frame in each direction. Moreover, the RC4 PRNG algorithm used by WEP includes an integrity check vector (ICV) to check the integrity of each packet. This process is summarized below.
First, WEP computes the ICV by performing a 32-bit cyclical redundancy check (CRC-32) of the frame and appends the vector to the original frame, resulting in the plaintext. Then, the message plus ICV is encrypted via the RC4 PRNG algorithm using a long sequence key stream - a long sequence of pseudorandom bits. This key stream is a function of the 40-bit secret key (which is shared between all authorized stations in the WLAN) and a 24-bit initialization vector (IV). Consequently, an exclusive-or (XOR) operation is made between the plaintext and the key stream to produce the ciphertext. Finally, it is the ciphertext that is sent over the radio link. Theoretically, the ciphertext provides data integrity because of the ICV and confidentiality due to encryption.
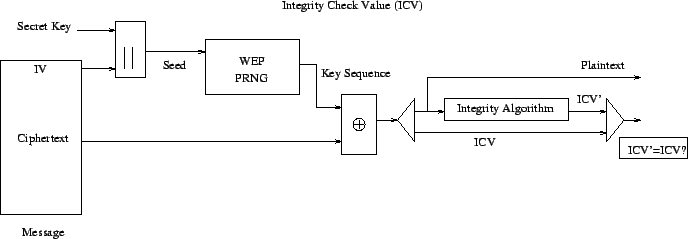
The receiver, inasmuch as RC4 PRNG algorithm is symmetric, performs the same procedure described above, but in reverse, to retrieve the original message frame. Specifically, the ciphertext is decrypted using a duplicated key stream to recover the plaintext. The recipient then validates the checksum on this plaintext by computing the ICV and comparing it to the last 32 bits of the plaintext, thus ensuring that only frames with a valid checksum will be accepted by the receiver.
WEP can be implemented with the classic 40-bit key and 24-bit IV or a vendor-dependent (hence proprietary) extended version that affords a larger key. The shorter key length can be relatively easy to compromise via brute-force attack, even with modest computing resources; however, a larger key such as the 128-bit keys would render brute-force attacks impossible, even for sophisticated computing systems. Nevertheless, alternative attacks are possible that do not require a brute-force strategy, thereby diminishing the strength of key length.
WEP depends on a secret key that is shared between the mobile stations (e.g. wireless Ethernet card) and access points (e.g. base station) to secure the transmitted frame). The secret key is 40 bits in length and the initialization vector (IV) that is randomly generated for each message is 24 bits, making the total key size 64 bits.
There are five simple steps to encrypting the packet frame, as shown in Figure 1:
The steps needed for decryption is similar to encryption, as shown in Figure 2:
As we discussed in our first progress report, there are a number of inherent insecurities in the Wired Equivalent Privacy (WEP) standard. There are a number of technologies that were developed as a step beyond this standard. They include various proprietary extensions to WEP, TKIP, AES, and 802.11i. We will discuss these solutions in detail, and describe how they will be used as new security solutions to eventually replace WEP.
First, there are a number of extensions to the WEP developed by various companies. These include Agere's WEPplus and 152-bit WEP and US Robotics' 256-bit WEP. Using a longer key makes it more difficult to crack, but the inherent insecurities in WEP still exist. For example, neither of the longer key lengths changes the short initialization vector problem. Agere claims that WEPplus does, but they also state that they only reduce the vulnerability, not remove it.
Second, a technology known as TKIP or the Temporal Key Integrity Protocol uses a dynamic scheme to change the key every 10,000 packets, so that a program like AirSnort can not simply gather data to determine a static key. However, TKIP still uses the RC4 encryption scheme, which may have been top of the line when WEP was created, but there are better schemes now. For the best encryption today, one would use AES, the Advanced Encryption Standard protocol. TKIP does provide a middle ground, however, as it could be implemented on present hardware using only a firmware update. The newest stadard, 802.11i needs new and better hardware to run properly.
Finally, 802.11i is the latest standard by the IEEE which attempts to provide the highest level of security for wireless networks. 802.11i is presently in committee, awaiting approval, but presently combines a dynamic key strategy like TKIP with a stronger encryption algorithm like AES to create a stronger security platform.
Ward, Mark. "Hacking with a Pringles Tube." BBC News 8 Mar. 2002. 17 Nov. 2002.
Flickenger, Rob. "Antenna on the Cheap (er, Chip)." O'Reilly Network 5 Jul. 2001. 17 Nov. 2002.
Louderback, Jim. "4 Simultaneous Channels Okay for 802.11b." Extreme Tech 15 Nov. 2002. 17 Nov. 2002.
"Wireless LAN Deployment and Security Basics" Extreme Tech. 17 Nov. 2002.
"Cisco Aironet Wireless LAN Security Overview: 802.1x Authentication." Cisco Website. 17 Nov. 2002.